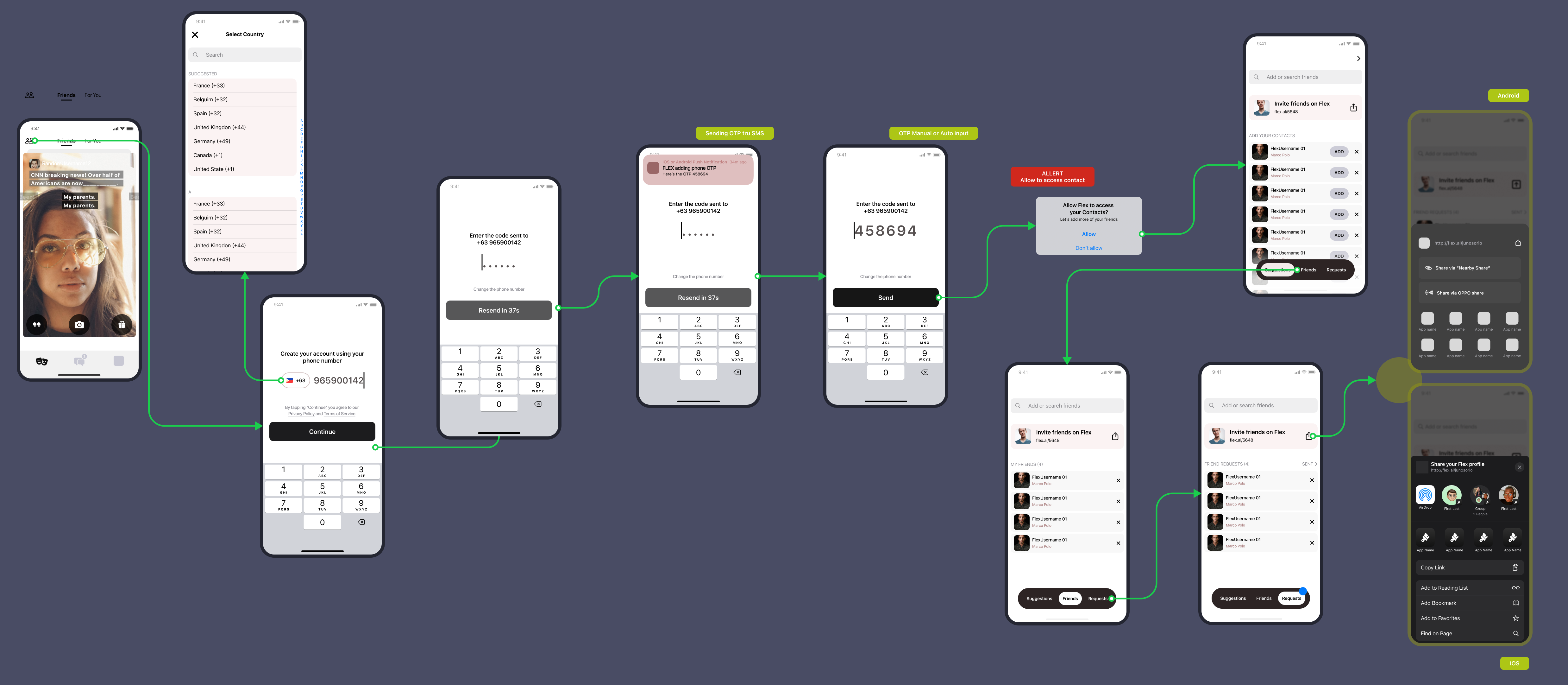
At first, I underestimated how tricky it would be. But as I dug deeper into real-world user behavior, security risks, and regional differences, I realized that designing a seamless OTP system is far more than just sending a code to a user’s phone.</br></br>
Here’s my journey, the challenges I faced, and the design decisions that made a difference.
Understanding the Importance of OTP in Applications
In today’s digital world, passwords alone are no longer enough. Research shows that:
- 81% of data breaches are due to weak or stolen passwords (Verizon Data Breach Investigations Report).
- 90% of IT managers consider adopting SMS-based OTPs or app-based authentication for added security.
- 50% of OTPs fail to reach users due to delivery issues, network failures, or user mistakes (Ponemon Institute).
However, while OTPs add an extra security layer, they also introduce potential friction. If a verification process is too slow, unreliable, or frustrating, users may abandon signup or login altogether. My goal was to create an OTP experience that was both secure and frictionless.
My Design Process: Creating a Seamless OTP Flow
1. Research & Understanding User Pain Points
Before jumping into design, I started by identifying common issues in OTP flows. Here’s how I gathered insights:
- Analyzed failure rates – I reviewed analytics to see where users were dropping off or failing OTP verification.
- Conducted user interviews – I asked users about their frustrations with OTP systems (e.g., slow delivery, unclear error messages).
- Explored country-specific challenges – Some countries have strict telecom regulations that delay or block OTPs. In places like India, users may prefer WhatsApp OTPs over SMS.
From my research, I found that the biggest issues were:
- Delayed OTPs (users waiting too long for a code).
- Input errors (mistyping OTPs, leading to frustration).
- Lack of alternative verification (users stuck if they never receive an OTP)
2. Prototyping & Iteration: Solving These Pain Points
Once I understood the problems, I created design solutions to address them.
Reducing Friction in OTP Entry
Instead of forcing users to type the OTP manually, I designed:
- Auto-fill support (detect OTPs from SMS and auto-fill them).
- One-tap copy-paste for emails (users can easily copy OTPs from email notifications).
Result: Reduced user errors and sped up verification.
Handling OTP Delays with Smart Alternatives
If an OTP wasn’t received within 15 seconds, we:
- Showed a resend option with a visible countdown.
- Suggested alternative methods: email verification or an authenticator app (depending on the country).
Result: Lower drop-off rates due to failed OTP deliveries.
Improving Error Messaging
Instead of generic messages like “Invalid OTP,” I designed clear, actionable feedback:
- OTP expired, request a new one.
- Incorrect OTP, please check and try again.
- Too many attempts—wait 30 seconds before retrying.
Result: Users understood what went wrong and how to fix it, reducing frustration.
3. Testing & Refining Based on Real User Behavior
Once the designs were in place, I tested them in real-world conditions:
- A/B Testing: Compared the new OTP flow against the old one to measure success.
- Analyzed completion rates: Tracked how many users successfully verified their accounts.
- Collected feedback: Listened to real users and iterated based on their experiences.
The impact?
- OTP completion rates improved by 18%
- Drop-off rates decreased by 12%
- Support tickets related to OTP failures reduced significantly

Final Thoughts: The Balance Between Security & Usability
Designing an OTP system was one of the most challenging but rewarding UX projects I’ve worked on. It taught me that:
- Security is important, but usability matters just as much. A frustrating OTP flow can drive users away.
- Not all users are the same. Country-specific differences (like telecom reliability) must be considered.
- Testing and iteration are key. Small tweaks, like auto-fill or clearer error messages, can make a big difference.
If you’re designing an OTP system, don’t just focus on security, focus on making it seamless, fast, and user-friendly.